3 Months Free Update
3 Months Free Update
3 Months Free Update
Which two functions are available for both inline and API protection? (Choose two.)
When using an out-of-band API connection with your sanctioned cloud service, what are two capabilities available to the administrator? (Choose two.)
Which two use cases would be considered examples of Shadow IT within an organization? (Choose two.)
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.
You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
You need to provide a quick view under the Skope IT Applications page showing only risky shadow IT cloud applications being used.
In this scenario, which two filter combinations would you use to accomplish this task? (Choose two.)
You want to prevent Man-in-the-Middle (MITM) attacks on an encrypted website or application. In this scenario, which method would you use?
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
Which two controls are covered by Netskope's security platform? (Choose two.)
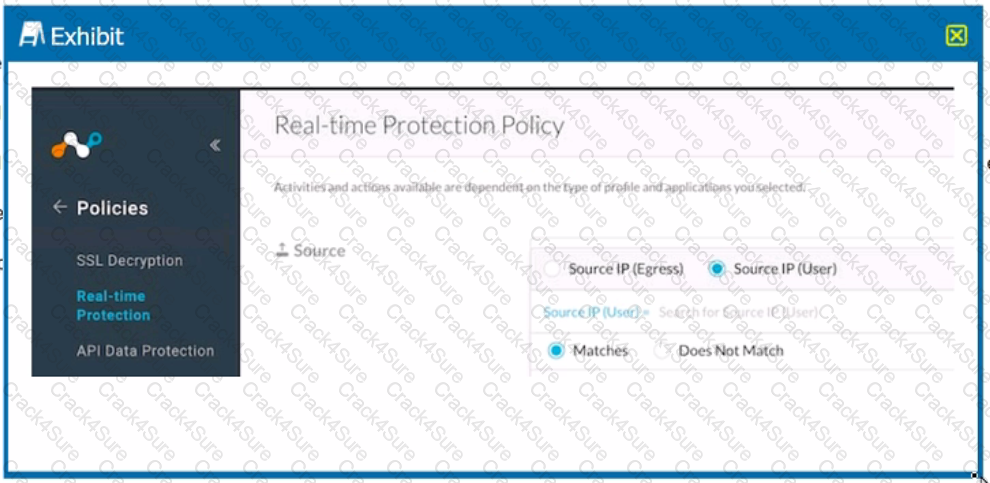
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
Exhibit

Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
A customer asks you to create several real-time policies. Policy A generates alerts when any user downloads, uploads, or shares files on a cloud storage application. Policy B blocks users from downloading files from any operating system (OS) other than Mac or Windows for cloud storage. In this case, policy A is least restrictive and policy B is more restrictive.
Which statement is correct in this scenario?